Cybereason GSOC has identified a malware infection exhibiting strong similarities to the previously reported Genesis Market malicious campaign that was dismantled by law enforcement in early 2023.
WHAT'S HAPPENING?
- Cybereason Security Services is investigating Lummastealer activity.
- Lummastealer drops Genesis Market malicious browser extension as the final payload.
- Genesis Market installs and executes its own JavaScript (JS) scripts on infected machines.
- These scripts are designed to systematically gather important information from victims' devices.
- The gathered data ensures consistent information is provided to the bots in Genesis Market's marketplace.
WHAT IS GENESIS MARKET
Genesis Market, which debuted in March 2018, has facilitated access to data from around 1.5 million compromised computers worldwide, offering over 80 million stolen account access credentials. The credentials for sale on Genesis Market include those linked to the financial sector, critical infrastructure, and various levels of government. Genesis Market has supplied the kind of access that ransomware attackers have used to target many organizations in the U.S., along with private sector organizations.
Genesis Market is an illicit online platform that has advertised and sold access credentials, stolen accounts, such as usernames and passwords for email, banking, and social media, all obtained from malware-infected computers worldwide.
Genesis Market was made to be user-friendly, allowing individuals to search for stolen credentials based on location and account type (including banking, social media, and email). In addition to accessing credentials, it offers device “fingerprints,” which are distinct combinations of device identifiers and browser cookies that can evade many websites' anti-fraud protections. This allows buyers to impersonate victims, tricking third-party sites into thinking they were the actual account owners.
Genesis Market has users spanning worldwide with over 225 countries. Federal law enforcement had been identifying users who bought and used stolen credentials for fraud and other cybercrimes. This effort has produced hundreds of leads for the FBI throughout the United States and for international law enforcement agencies. As part of this initiative, the operation known as Operation Cookie Monster, allowed authorities to seize 11 domain names that were integral to Genesis Market’s infrastructure, based on a warrant authorized by the U.S. District Court for the Eastern District of Wisconsin.
CRITICAL TAKEAWAYS
The malicious Genesis extension performs the following actions:
- Targets browsers like Chrome, Opera, Brave, and Microsoft Edge.
- Collects browser data and sends it to the C2 server.
- Sets up a reverse proxy (ws://<reverseProxyDomain>:4343).
- Resolves the C2 server using Blockchain transactions.
The extension accessed the following browser data:
- Browser clipboard data
- Cookies
- History
- Current open tabs
- Email data (outlook.live, mail.yahoo, mail.google)
- Clipper data
- YouTube channel data
- Crypto exchange and Crypto wallet
- Coinbase wallets
- Facebook Payment data
- Google pay
- Installed extensions
- User-agent data
- Screenshots of the browser page at defined time intervals
- File system data
Analysis
Overview
Cybereason detected a Genesis market - Malicious Browser extension payload as part of the Lumma Infostealer activity.

Attack flow diagram related to Genesis Market - Malicious Browser Extension
The Lumma Infostealer group uses a setup/installer file as part of this attack. The victim downloads the initial payload(Zip file) from social engineering/phishing websites. The Zip file (e.g., v6.20.0_installer_x64_.zip) includes an MSI file (e.g., app__v6.20.0_.msi), which is packaged with these files:
- Executable file (Ex: nvidia geforce experience.exe)
- Archive file (RAR format)
The RAR file holds a second-stage LummaStealer DLL. During the MSI installation (via msiexec.exe), it launches the included executable (e.g., nvidia geforce experience.exe), which then:
- Loads the LummaStealer DLL using techniques like DLL side-loading or DLL hollowing.
- Kicks off a child process (powershell.exe) to run the following script.
- The script connects to the C2 domain (e.g., root-head[.]com) and retrieves a Base64-encoded third-stage payload (2709.bs64).
 PowerShell script to download the base64 encoded Malicious Browser Extension
PowerShell script to download the base64 encoded Malicious Browser Extension
The decoded third-stage payload is a Powershell script with added layers of obfuscation.
 Attack Tree
Attack Tree
The decoded PowerShell script deploys the malicious Genesis Market browser extension and sends user data to C2 domains managed by the attacker.
Base64 Encoded Powershell Analysis
The PowerShell script attempts to install a malicious browser extension across multiple browsers, including Chrome, Microsoft Edge, Opera, and Brave. It carries out these steps:
- Launches the browser processes for Chrome, Microsoft Edge, Opera, and Brave.
- Creates a new folder and installs the Javascript.
- Modifies the Secure Preferences JSON file to ensure the extension activates automatically upon browser restart, enabling persistence.
- Targets these specific directories:
- Google\Chrome\User Data
- BraveSoftware\Brave-Browser\User Data
- Microsoft\Edge\User Data
- Opera Software\Opera Stable
- The extension has permissions (Active/Granted) to access the following data:
{"api":["activeTab","alarms","clipboardRead","clipboardWrite","cookies","history","management","notifications","storage","system.display","system.storage","tabs","unlimitedStorage","webNavigation","webRequest","system.cpu","system.memory","declarativeNetRequest","scripting"],
The extension is set to access all URLs:
["*://*/*","<all_urls>","http://*/*","https://*/*"]
Extension Path is:
C:\\Users\\User\\Desktop\\1408\\drop-builder\\extension2
- The javascript payloads are stored as base 64 encoded data. The Powershell script will decode the data and install the extension. The base64 encoded data contains the following Javascript files
|
src\finder\initializeFinder.js
|
modules\content-scripts-register-polyfill.4.0.0.js
|
src\background.js
|
|
src\finder\instructions.js
|
src\content\clipboard.js
|
src\content\main.js
|
|
src\finder\matches.js
|
src\finder\extract.js
|
src\finder\helpers.js
|
|
src\finder\traverse.js
|
src\finder\zip.js
|
src\functions\clipper.js
|
|
src\functions\commands.js
|
src\functions\csp.js
|
src\functions\domain.js
|
|
src\functions\exchangeSettings.js
|
src\functions\extensions.js
|
src\functions\getMachineInfo.js
|
|
src\functions\injections.js
|
src\functions\notifications.js
|
src\functions\proxy.js
|
|
src\functions\screenshot.js
|
src\functions\screenshotRules.js
|
src\functions\settings.js
|
|
src\functions\tabs.js
|
src\functions\utils.js
|
src\mails\gmail.js
|
Browser Extension Analysis
The malicious browser extension installs the “Save to Google Drive” extension and saves web content or screen capture directly to Google Drive. A background key is defined to run the script(/src/background.js) in the extension's background page.
The following response headers were removed to access the browser’s Document Object Model (DOM).
- Content-security-policy: Mitigates Cross-Site Scripting (XSS) attacks
- Content-security-policy-report-only: Allows web developers to send CSP violation reports
- X-webkit-csp: Content security policy for WebKit-based browsers
- X-frame-options: Prevents the site from clickjacking attacks
Javascript Analysis
src\background.js
Creates a new alarm for the current browser session. These browser alarms are designed to trigger code execution at designated times. The alarms listed below were established to connect with C2C:
- checkCommands
- checkProxy
- updateDomain
- checkInjections
Also calls many functions from the other javascript files.
src\content\clipboard.js
Copies the textual contents of the system clipboard and writes the specified text to the system clipboard.
src\content\main.js
Retrieves data from sources like Google Payment, YouTube channels, Crypto Wallet (Exchange), and Facebook Payment. Captures screenshots at set intervals and runs the script.

main.js code snippet
src\finder\extract.js
Pulls files from a directory, examines their details, and reads the file stream.
src\finder\helpers.js
Queries the machine user list and creates a new user(C:/Users/)
Compiles retrieved data into a ZIP file and transmits it to the server: hxxps://true-lie[.]com/api/machine/set-files-v
 POST request - true-lie[.]com
POST request - true-lie[.]com
src\finder\traverse.js
Locates files within a directory and navigates through files and folders in the file system.
src\functions\commands.js
Fetches the commands from the attacker URL: Attackerdomain/machine/commands?uuid=uuid
Commands issued:
- Extension: call setEnableExtension, initMachine functions
- info: call getInjections, getSettings, initMachine functions
- push: call createNotification function
- Cookies: Gets all the cookies from the browser
- Url: call openUrl
- Current_url: call getCurrentTab
- History: call getHistory
- Injects: call getInjections
- Clipper: call getClipperData
- Settings: call getSettings
- Proxy: Call setIsEnabled to enable proxy
- Screenshot_rules: call getScreenshotRules
The command output is sent back to the attacker using a POST method.
 POST request
POST request
src\functions\csp.js
Disables Content Security Policy (CSP). CSP helps detect cross-site scripting (XSS) and data injection attacks.
src\functions\domain.js
The C2 domains were resolved using blockchain transactions. The following C2 domain was detected:
bc1q4fkjqusxsgqzylcagra800cxljal82k6y3ejay - gzipdot[.]com
- Sample Links: hxxps[:]//mempool[.]space/api/address/bc1q4fkjqusxsgqzylcagra800cxljal82k6y3ejay/txs
- hxxps[:]//" + _0x41d66f[_0x1c70b5] + "/api/machine/sign?d=

 C2 Domain Resolution
C2 Domain Resolution
src\functions\exchangeSettings.js
Retrieves data from the attacker domain to exploit Exchange/Coinbase wallets, Facebook Payment page, Youtube channel page, and Google Pay page.
src\functions\extensions.js
Queries the installed apps/extensions and enables the malicious extension
src\functions\getMachineInfo.js
Provides information about the app or extension based on its manifest, gathers all cookies from a specific cookie store, and collects the user agent string along with details about the current browser, host operating system, and hardware setup.
Sends a POST request to the URL: Attackerdomain/machine/init.
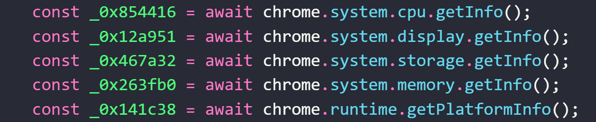
Machine CPU, Memory, OS data retrieval
src\functions\injections.js
Injection data is fetched from the attacker URL: domain/machine/injections?uuid=”uuid”. Gathers details about all active windows and verifies if the URL matches:
- payments.google
- adsmanager.facebook.com
- hxxps://accounts.google.com
- hxxps://consent.youtube.com

Google/Youtube Account access
src\functions\notifications.js
Creates a custom notification and a new tab.
src\functions\proxy.js
Toggles between startProxy() and stopProxy() function. A new WebSocket object is created and the reverse proxy(ws://<reverseProxyDomain>:4343) connection is established. The Websocket object creates a communication session between the user's browser and a server.

Reverse Proxy
A custom HTTP request is crafted by adjusting the headers, secret token, and cookie. Finally, the HTTP request is sent to: URL/redirect-hack.html?id= and the request is redirected to the attacker domain via(redirect-hack.html).
src\functions\screenshot.js
Captures a screenshot of the visible area of the currently active tab in the specified window.
src\functions\settings.js
Extension settings are retrieved from the attacker URL: domain/machine/settings
src\functions\tabs.js
Collects all information about the current tab, opens a new tab with a given URL, and pulls up the browser history.
 Tab/ History Data
Tab/ History Data
src\mails\gmail.js
Gathers email data (pulling the Subject, email addresses, and content for each email shown) from the current page on platforms like outlook.live, mail.yahoo, or mail.google. Scans for emails containing verification codes to sidestep two-factor authentication.
 Verification Email Search
Verification Email Search
IOCs Associated with Post-Exploitation
We detected the following list of IoCs associated with Browser Extension payload:
|
Type
|
Value
|
Comment
|
|
Sha1
|
95d2980786bc36fec50733b9843fde9eab081918
|
obs-ffmpeg-mux.exe
|
|
359354ea44356f2ddea3f2c8bc558810533f95be
|
kafkjo.rar
|
|
c07e49c362f0c21513507726994a9bd040c0d4eb
|
app__v7.2.8_.msi
|
|
9f3b02b148aa17094e7a13dbba3b49a279e12e80
|
v7.2.8_installer_x64_.zip
|
|
0cbca4dbbdcb61e8336753bdabda33b56c51c52e
|
v6.20.0_installer_x64_.zip
|
|
b08f8b87efc450368816c769c8c1c54ff6da53b9
|
nvidia geforce experience.exe
|
|
d363b062d0d8df89449faa0b9ac2e6e578054696
|
app__v6.20.0_.msi
|
|
IP
|
104.21.16[.]110
|
Resolves to hit-kick[.]com
|
|
172.67.210[.]204
|
Resolves to hit-kick[.]com
|
|
104.21.53[.]8
|
Resolves to sergei-esenin.com
|
|
104.21.80[.]87
|
Resolves to l-back[.]com
|
|
172.67.176[.]159
|
Resolves to l-back[.]com
|
|
104.21.13[.]217
|
Resolves to last-blink[.]com
|
|
URL
|
last-blink[.]com/2709[.]bs64
|
URL to download base64 encoded data
|
|
root-head[.]com/25082[.]bs64
|
URL to download base64 encoded data
|
|
exilepolsiy[.]sbs
|
C2 Domain
|
|
laddyirekyi[.]sbs
|
C2 Domain
|
|
isoplethui[.]sbs
|
C2 Domain
|
|
offeviablwke[.]site
|
C2 Domain
|
|
ghostreedmnu[.]shop
|
C2 Domain
|
|
gutterydhowi[.]shop
|
C2 Domain
|
|
offensivedzvju[.]shop
|
C2 Domain
|
|
reinforcenh[.]shop
|
C2 Domain
|
|
gzipdot[.]com
|
C2 Domain
|
|
true-lie[.]com
|
C2 Domain
|
Cybereason Recommendations:
- Isolate and determine if forensic analysis will be performed. If yes, a forensic image (preservation copy) should be created for analysis to determine the scope of potential data at risk and the extent of threat actor activity. If no, proceed with internal/existing IT processes to restore to "gold image" (baseline)."
- Conduct a forensic analysis of the "at risk" data as identified within this article under Critical Takeaways section under "The extension accessed the following browser data:" which details specifically what data elements may be at risk and should be considered for inventorying, resetting, and potential follow-on investigation into unauthorized or unexpected activity.
- Inform users about the deceptive captcha page or "click fix" that prompts them to copy and paste a PowerShell script.
- Add the Lumma infostealer C2 domains to the firewall’s outbound blocklist.
MITRE ATT&CK MAPPING
|
Tactic
|
ATT&CK Technique (ID)
|
|
Initial Access
|
T1566 Phishing
|
|
Execution
|
T1204.002 User Execution: Malicious File
T1059.007 Command and Scripting Interpreter: Javascript
|
|
Persistence
|
T1176 Browser Extension
|
|
Defense Evasion
|
T1055.012 Process Injection: Process Hollowing
T1027.013 Encrypted/Encoded File
|
|
Credential Access
|
T1539 Steal Web Session Cookie
|
|
Discovery
|
T1082 System Information Discovery
|
|
Collection
|
T1113 Screen Capture
|
|
Command and Control
|
T1071.001 Application Layer Protocol: Web Protocols
|
ABOUT THE RESEARCHERs
Hema Loganathan, T2 GSOC Analyst

Hema Loganathan is a GSOC Analyst with the Cybereason Global SOC team. She is involved in MalOp Investigation, Malware Analysis, Reverse Engineering, and Threat Hunting. Hema has a Master of Science degree in Information Systems.
Peter Moote, T2 GSOC Analyst

Peter Moote is a GSOC Analyst with the Cybereason Global SOC team. He is involved with threat hunting, Malop investigation and remediation. His professional certifications include GCIH and GPEN.





 PowerShell script to download the base64 encoded Malicious Browser Extension
PowerShell script to download the base64 encoded Malicious Browser Extension Attack Tree
Attack Tree
 POST request - true-lie[.]com
POST request - true-lie[.]com POST request
POST request
 C2 Domain Resolution
C2 Domain Resolution


 Tab/ History Data
Tab/ History Data Verification Email Search
Verification Email Search


